We Feel You
Managing the explosion of machine connections with limited budgets, rising cyber risks, and the constant pressure to move faster and stay ahead of the competition.
We Got You
With backing from DoD and DOE, Operant has developed the first Data-Centric approach proven to radically reduce complexity, risks, and costs.
Zero Trust for Machines
Our mission is to empower enterprise teams to unleash their digital workforce with solutions that drive both security and efficiency:
-
Strong Authentication: Every machine, AI agent, workload, and edge device is assigned a unique, verifiable identity.
-
Access Controls: Once authenticated, policies are enforced to define who can access what, when, and how.
-
Trust Administration: An intuitive abstraction layer that simplifies complexity, while seamlessly integrating with existing systems and team workflows.
Multi-Party Trust (MPT) Platform
Universal Trust Fabric that offers an equivalent of two-factor authentication and access controls, but for various types and classes of non-human machine interactions
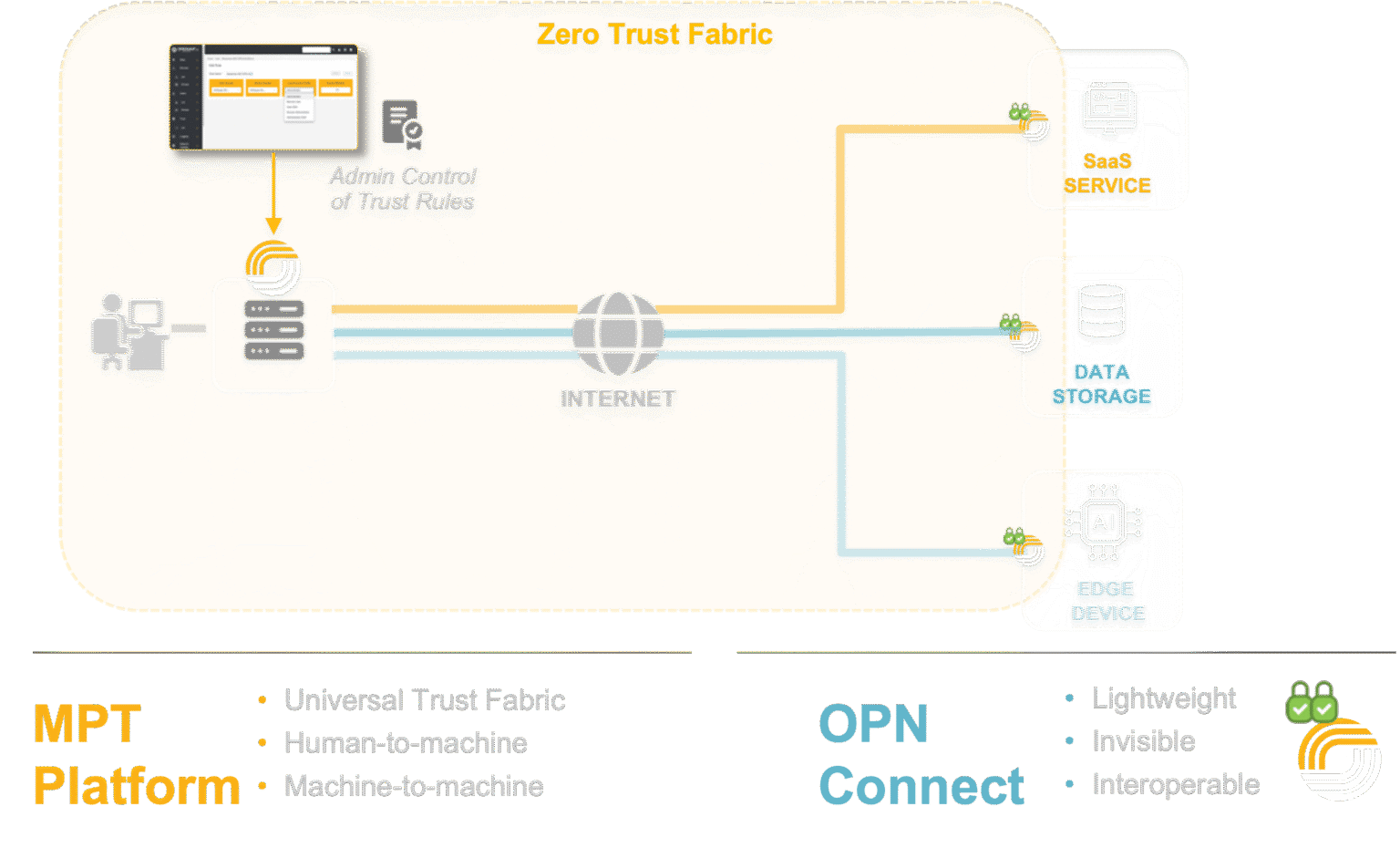
Human-to-Machine
Single sign-on access management between people and machines
Machine-to-Machine
Segment and authenticate data flows and workloads
Agent-to-Agent
Extend access controls between AI systems, services, and databases
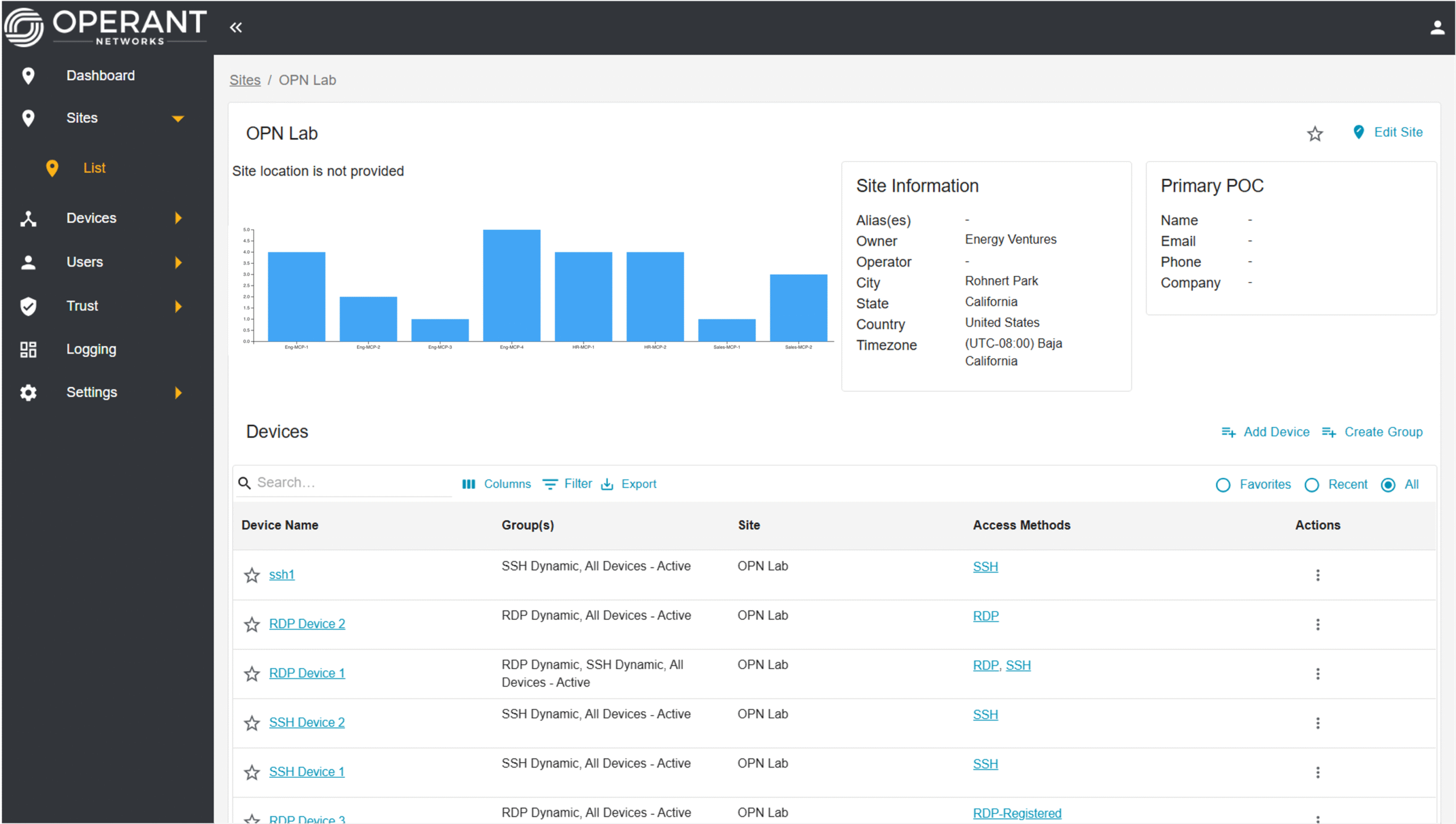
Operant's Multi-Party Trust (MPT) platform provides visibility and efficient management across all categories of non-human machines, including edge devices, workloads, and agents. Its intuitive interface enables analysts to seamlessly set up, configure, and troubleshoot issues.
The integrated Zero Trust architecture allows enterprises to easily enforce fine-grained access controls, ensuring secure trust management across departments, partners, and vendors.
Mitigate cyber-risks
Operational Visibility
Ensure Data Privacy
Simplify the distribution and lifecycle management of secrets and credentials
Interactions receive mutual authentication, data encryption, and single use credentials
Deny-by-default approach approved for specific actions to authenticated things
Updates and Insights from the Operant Team
Want to know more?
Get in touch and we'll get back to you as soon as we can. We look forward to hearing from you!
Our location
Operant Networks
1500 Valley House Dr
Suite 210
Rohnert Park, CA 94928